- Berkeley Electronic Press Selected Works.
- Using Cain and the AirPcap USB adapter to crack WPA/WPA2 This video introduces the viewer to the AirPcap USB adapter, and auditing WiFi networks with it. If the embedded video below does not show RIGHT click here to save the file to your hard drive. Printable version of this article.
My favorite program to use is cain and abel it has a good brute force cracker and a large amount of dictionary force tatics i reccommend that it can crack any wep with in min, i ve had it break some small WPa but like im tryong to make my way up to cracking a 128 bit wpa but aircrack is always the best thing by me.
Table of Contents
- 1. What is Password Cracking?
- 2. Cracking Ideas Overview
- 3. Some Well Known Cracking Tools
- 4. Password Cracking using Cloud Services
- 5. Lab Experiments on Passwords and Cracking
1 What is Password Cracking?
Given an 'encoded' (may be salted) password, (re-) construct its plaintext version. A login Trojan, a keyboard logger, un-encryptedcommunication with an ISP or website, …, can all get the plain textpassword. We (should) call this stealing – not cracking.
Prerequisite: ../Passwords/ hashes, salting, MD5, SHA512, Linux /etc/shadow
1.1 Caution
When you crack passwords, you could be breaking the law. Doit only in the context of our course.
1.2 Overview
- Terminology: Lookup Tables, password lists, crack hashes.
- https://haveibeenpwned.com/ Check if you have an account that hasbeen compromised in a data breach!
- https://www.onlinehashcrack.com/ A password recovery serviceassisting pen-testers & security experts since 2008. Non-profit.
- Penetration testing includes password audit.
- https://www.kali.org/news/kali-linux-aws-cloud/ December 2016Kali Linux full images are free on the Amazon AWS marketplace.Make sure to fill out the Amazon penetration testing request form.
- https://github.com/offensive-security/kali-cloud-build Kalibootstrapping script for Amazon Machine Images (AMI)
- There are many other penetrations distros. Visithttp://distrowatch.com
2 Cracking Ideas Overview
2.1 Stealing the Passwords
A login Trojan, a keyboard logger, un-encrypted communication with anISP or website, …, can all get the plain text password. We (should)call this stealing – not cracking.
2.2 Social Engineering
- [From 'The New Hacker's Dictionary' aka Jargon File] Socialengineering is a term used among crackers and samurai for stealing(cracking?) techniques that rely on weaknesses in wetware ratherthan software; the aim is to trick people into revealing passwordsor other information that compromises a target system's security.
- Classic scams include phoning up a mark who has the requiredinformation and posing as a field service tech or a fellow employeewith an urgent access problem.
2.3 Causing a Password Reset
- A now common stealing (cracking?) technique is to attempt to loginat a site, and cause a password reset request to be sent to theemail address on record, which the attacker has gathered throughother techniques. This email is then intercepted.
2.4 Fooling Finger Prints
Read smartphone fingerprint scanners are they secure?. Read also HowTo Fool a Fingerprint Security System athttp://www.instructables.com/. Does this really work? May be notalways. But, as can be seen, this is mostly a question of perfectingsuch techniques. Here is more advice: why you should not use the newsmartphone fingerprint readers.
2.5 What Are Hashes?
- What exactly are rainbow tables cannot be explained without firsttalking about crypto hashes, hash chains etc.
- Hash functions are used in data bases, etc. Every hash functionmaps a large domain into a small range of numbers. Thus, therealways will be collisions, i.e., for two a, b, (hash) = hash(b).Note also that the inverse of a hash function is not a function.
- Crypto-hash functions, chash, are used in storing passwords, etc.A few famous crypto hash functions are MD5, SHA1, SHA512. Everycrypto hash function is an ordinary hash function also.
- The result r of chash(a) is known as a hash of a. The r is notconsidered an encryption of a.
- The crypto hash functions are so carefully designed/ constructed/implemented that, until recently (?), there was no 'computationallyfeasible' algorithm that can be applied to the following problem.Because of this they are also called one-way.
- Suppose we already know, chash(a) = y, where a is a plain textinput, and y was the result of a crypto-hash function chash.Discover a b so that: chash(b) = y.
- For MD5 and SHA1, in the last few years, the above problem has beensolved.
2.6 Dictionary Attack
- Brute force 'decryption'
- Crackers obtain
/etc/passwdand/etc/shadowfiles through othertechniques, and crack the encoded passwords on their own computersystems. - To speed up password cracking, a dictionary of words and well-knownpasswords are encoded using all possible salt values. These arecompared with the encoded passwords in the
/etc/shadowfile.These are compared with the encoded passwords in the/etc/shadowfile. Several machine-readable collections of dictionaries areavailable for various uses, including cracking. - An 8 character password encodes, with salt, to one of 4096 * 13character strings. So, a dictionary of say 2,000,000 common words,names, passwords, and simple variations would amount to some 20 GB.
2.7 Rainbow Tables
- ./Rainbow-Tables What are Rainbow Tables? These use good amount ofdiscrete math.
2.8 Cracking Services
- https://haveibeenpwned.com/ Check if you have an account that hasbeen compromised in a data breach!
- https://www.onlinehashcrack.com/ 'Online Hash Crack is a passwordrecovery service assisting pen-testers & security experts since2008.' Non-profit.
3 Some Well Known Cracking Tools
- Crack programs now use GPUs (visit e.g.,http://www.cryptohaze.com/) in parallelizing and can try billionsof hashes per second.
- http://sectools.org/tag/pass-audit/ Password Audit tools. Rankedby votes.
3.1 John-the-Ripper
- JTR is a password cracker. Linux/Unix, Windows. Command line.
apt-get install johnInstallsjohn,unshadow, etc.https://github.com/magnumripper/JohnTheRipper - Suppose we have a file of salted and encoded passwords, such as/etc/shadow of Linux. John can try hard to crack these into plaintext. Can take hours.
- Attempts (i) a dictionary attack, (ii) combined dictionary words,(iii) hybrid attack of dictionary words with special characters andnumbers, (iv) brute force.
- John prints a status line when a key is pressed. John can createmultiple named sessions. http://www.openwall.com/john/doc fulldocs, including download links, etc.
- http://rafaveguim.github.io/cracking/passwords/jtr/2016/05/05/jtr-research-lab/ Generate charts with
--external=AutoStatusandchart_logs.py. 2016.
3.2 Hashcat
- Hashcat is a 'password recovery' utility, using CPUs, GPUs, andother hardware accelerators on Linux, Windows, and OSX. Can dodistributed password cracking.
3.3 RainbowCrack
- http://project-rainbowcrack.com/ RainbowCrack uses rainbow tablesto crack unsalted hashes. It differs from brute force hashcrackers. GPU acceleration is a key feature of RainbowCrack. Itcan offload most runtime computation to GPUs (NVIDIA/ AMD).
- http://project-rainbowcrack.com/table.htm A List of RainbowTables. Key space of 13,759,005,997,841,642. Several TB ofgenerated rainbow tables for LM, NTLM, MD5 and SHA1 are listed.Not (all) free.
- http://project-rainbowcrack.com/ has freely downloadableexecutables for all major OS:
- rtgen: generate rainbow tables,
- rsort: sort the rainbow table;
- rcrack: find the password.
3.4 CrackStation
- https://crackstation.net/ CrackStation uses massive pre-computedlookup tables created by extracting every word from the Wikipediadatabases and adding with every public password list.
- Buy crackstation-wordlist password-cracking dictionary. Theirlookup table implementation (PHP and C) is available athttps://github.com/defuse/crackstation-hashdb
3.5 Hydra
- Attempting to visit http://www.thc.org/ may produce the ominousGoogle warning: 'The site ahead contains harmful programs'.Personally, I think, this site is safe to visit. But, go withyour own instincts.
- 'Hydra is a parallelized login cracker which supports numerousprotocols to attack. It is very fast and flexible, and new modulesare easy to add. This tool makes it possible for researchers andsecurity consultants to show how easy it would be to gainunauthorized access to a system remotely.'
- 'When you need to brute force crack a remote authenticationservice, Hydra is often the tool of choice. It can perform rapiddictionary attacks against more than 50 protocols, includingtelnet, ftp, http, https, smb, several databases, and muchmore. Like THC Amap this release is from the fine folks atTHC.' – http://sectools.org/tool/hydra/
apt-get install hydrahttps://www.thc.org/thc-hydra/ ;https://github.com/vanhauser-thc/thc-hydra;http://tools.kali.org/password-attacks/hydra- THC-Hydra http://sectools.org/tool/hydra/ 'When you need to bruteforce crack a remote authentication service, Hydra is often thetool of choice. It can perform rapid dictionary attacks againstmore than 50 protocols, including telnet, ftp, http, https, smb,several databases, and much more.' Multi platform.
- Hydra can generate passwords.
Read the manual for details.
- Cracking
hydra -l pmateti -P passwordhashes.txt 192.168.17.223 ssh
3.6 Brutus
- Brutus https://github.com/mjosaarinen/brutus is an open sourceonline password cracking tool. For both Linux and Windows. HTTP,POP3, FTP, SMB, Telnet, IMAP, NNTP, NetBus, etc.
3.7 Medusa
apt-get install medusa- http://foofus.net/goons/jmk/medusa/medusa.html Medusa ParallelNetwork Login Auditor.
3.8 L0phtCrack/ Ophcrack
- Ubuntu:
apt-get install ophcrackhttp://ophcrack.sourceforge.net/ - OphCrack is a free rainbow-table based password cracking tool forWindows, Linux and MacOS. It cracks LM and NTLM hashes. Free andpremium rainbow tables. It is among the most popular Windowspassword cracking tools (Cain and Abel is probably the mostpopular; see below).
- L0phtCrack is an alternative to OphCrack. It attempts to crackWindows passwords. It also uses dictionary and brute force attacksfor generating and guessing passwords.
- L0phtCrack was acquired by Symantec and they promptly discontinuedit in 2006. Later, L0phtCrack developers re-acquired this tool andre-released it in 2009.
3.9 PACK
- http://thesprawl.org/projects/pack/ Password Analysis and CrackingKit (PACK) of Defcon 2010.
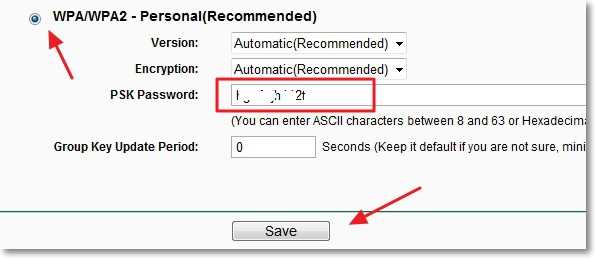
3.10 Cain-and-Able For Windows
Cain And Abel Crack Wpa2 Encryption Download
- http://www.oxid.it/ last release 2014; Cain and Abel is a password'recovery tool' for Windows. 'It allows easy recovery of variouskind of passwords by sniffing the network, cracking encryptedpasswords using Dictionary, Brute-Force and Cryptanalysis attacks,recording VoIP conversations, decoding scrambled passwords,recovering wireless network keys, revealing password boxes,uncovering cached passwords and analyzing routing protocols.'
- 'Cain and Abel can crack passwords using a dictionary attack,rainbow attack, and brute force. … It is also a great ARPPoisoning and MiTM tool.'
3.11 Aircrack-Ng
- http://www.aircrack-ng.org/ Aircrack-NG can crack WEP or WPA2passwords. It uses the FMS attack along with other useful attacktechniques for cracking password. For Linux and Windows. Capableof creating an Evil Twin, etc.
3.12 Miscellaneous
- http://wfuzz.org/ + https://github.com/xmendez/wfuzz Wfuzz is a Pythonbased flexible web application brute forcer which supports variousmethods and techniques to expose web application …
- Crack programs now use GPUs (visit e.g.,http://www.cryptohaze.com/) in parallelizing and can try billionsof hashes per second.
- Application Specific Crack tools
- http://sectools.org/tag/pass-audit/ Password Audit tools. Rankedby votes.
4 Password Cracking using Cloud Services
4.1 CrackStation

https://crackstation.net/CrackStation uses massive pre-computed lookup tables to store amapping between the hash of a password, and the correct password forthat hash.

'The hash values are indexed so that it is possible to quickly searchthe database for a given hash. If the hash is present in the database,the password can be recovered in a fraction of a second. This onlyworks for 'unsalted' hashes. For information on password hashingsystems that are not vulnerable to pre-computed lookup tables, see ourhashing security page.'
Crackstation's lookup tables were created by extracting every wordfrom the Wikipedia databases and adding with every password list wecould find. We also applied intelligent word mangling (brute forcehybrid) to our wordlists to make them much more effective. For MD5 andSHA1 hashes, we have a 190GB, 15-billion-entry lookup table, and forother hashes, we have a 19GB 1.5-billion-entry lookup table.
4.2 Kali Linux on Cloud
- https://www.kali.org/news/kali-linux-aws-cloud/ December 2, 2016'We’re happy to announce that we’ve once again listed our KaliLinux images on the Amazon AWS marketplace. You can now spin up anupdated Kali machine easily through your EC2 panel. Our currentimage is a “full” image, which contains all the standard toolsavailable in a full Kali release. Once your instance is running,connect to it with your SSH private key using the “ec2-user”account. Don’t forget to update your Kali instance to get thelatest packages and bug fixes. Type as root (or sudo): apt update&& apt dist-upgrade. We are “selling” these images on themarketplace for free, so other than the regular Amazon charges,there are no extras to pay. The Kali team would like to take thisopportunity to thank r0kh for his efforts of getting Kali back ontrack (no pun intended) and working flawlessly in AWS. If you planto use these Kali images for penetration testing in an AWSenvironment, make sure you check out the Amazon penetration testingrequest form.'
- https://www.kali.org/news/azure-marketplace-weekly-iso-builds/ September 13, 2016
- https://github.com/offensive-security/kali-cloud-build Kalibootstrapping script for Amazon Machine Images (AMI)
5 Lab Experiments on Passwords and Cracking
Objectives: To help you gauge the level of security offered by thetypical password systems. The goal is to crack as many passwords aspossible in the inputs described below. This can take hours on fastlaptops/ desktops in 2017, if you do not take advantage of multiplecores or GPU. Our goal in cloud computing is to crack as fast aspossible.
Record how many pass words can be cracked and how fast. Try John theRipper and one other of your own choice.
The following summarizes./password-labs.html
5.1 Example Inputs
- You may want to construct your own examples of the passwd andshadow files, where you know the passwords you used.
- Design a password that is not crackable by any of the tools.
5.1.1 Example #1 Three User Names and Passwords
- MD5 examples shown from machine M1 in the
/etc/shadowfileformat. Just three entries.
5.1.2 Example #2 from a Real Linux Machine Setup
- ./Linux/etc/shadow file is taken from one of our lab accounts froma previous term. Uses salted MD5.
5.1.3 Example #3: SHA512 Password Hashes
- Since MD5 is considered 'broken', Linux distributions have moved tousing salted SHA512 password hashes (crypt id 6, i.e.,
$6$),which are several orders of magnitude more difficult to brute-forceor generate rainbow tables for. Example lines from machine M2: - The lines below are the same as above but split into muliple linesfor readability:
How Secure Is Wpa2 Encryption
5.2 Password Cracking Word Lists
- The following are readily available 'word lists' in the context ofchoosing good passwords. This is obviously not an exhaustivelist. Note also that some files are populated at multiple sites.These are collections of broken password databases.
/usr/share/wordlists/*of the Kali Linux distribution.- ./500-worst-passwords.txt Worst passwords that were actually in use.
- http://weakpass.com/lists More of the above kind. A largecollection. Totaling in the GB range.
- https://github.com/danielmiessler/SecLists/ is the securitytester's companion. It is a collection of multiple types of listsused during security assessments. List types include usernames,passwords, URLs, sensitive data grep strings, fuzzing payloads, andmany more. It includes a collection of password lists. Itincludes the RockYou lists.
- http://contest-2010.korelogic.com/wordlists.html wordlists used in'Crack Me If You Can' contest of DEFCON 2010.
- https://wiki.skullsecurity.org/Passwords Passwords that were leakedor stolen from sites.
- http://www.justpain.com/ut_maps/wordlists/ Not just passwords.Words tokenized from books, etc.
- http://www.adeptus-mechanicus.com/codex/hashpass/hashpass.php Hashdumps and Passwords 2014
- http://www.openwall.com/wordlists/ 'This wordlists collection is aresult of processing many hundreds of public domain wordlistfiles.' Full version is not free. The reduced freely downloadableversion is available at https://download.openwall.net/pub/.
- Mark Burnett, Today I Am Releasing Ten Million Passwords, 2015.'This is completely absurd that I have to write an entire articlejustifying the release of this data out of fear of prosecution.'
5.3 Cracking Tools
- Download (or find/ discover in Kali/ BT5) at least two passwordcracking programs. You can find several by searching the web.
- Depending on the tools downloaded, you will need to builddifferently. Do this as an ordinary user, not as root, unlessimpossible. You may also need to download 'dictionaries' for useby the tools.
- John the Ripper (
john) is a fast password cracker.
6 References
- http://fsecurify.com/using-ordered-markov-chains-and-user-information-to-speed-up-password-cracking/ Reference
- http://www.admin-magazine.com/Articles/John-the-Ripper CheckingPassword Complexity with John the Ripper, 2013? Recommended Reading
- https://labs.mwrinfosecurity.com/blog/a-practical-guide-to-cracking-password-hashes/ Recommended Reading
- http://rafaveguim.github.io/cracking/passwords/jtr/2016/05/05/jtr-research-lab/ Uses hashcat, hashcat utils and PACK. Reference
7 End
Lot's of users searching for wireless hacking tricks and tips, I already explained WPA2 hacking almost impossible but still WPA & WEP hacking possible, so I decide to share all top software and tools to exploit these type of connections.
Complete Tools For WEP and WPA Wireless Cracking:
Wpa2 Best Encryption Why
1- Aircrack :
Aircrack is a standout amongst the most mainstream wireless passwords cracking tools which you can use for 802.11a/b/g WEP and WPA cracking. Aircrack utilizes the best calculations to recoup wireless passwords by catching bundles. When enough bundles have been assembled, it tries to recuperate the secret word. To make the assault speedier, it executes a standard FMS assault with a few advancements.
Cain And Abel Crack Wifi Password
The organization behind the device likewise offers an online instructional exercise where you can figure out how to introduce and utilize this apparatus to break wireless passwords. It comes as Linux appropriation, Live CD and VMware picture choices. In the event that you are not happy with Linux, you will think that it difficult to utilize this apparatus. For this situation, attempt Live CD or VMWare picture. VMWare Image needs less information, yet it just works with a restricted arrangement of host OS, and just USB gadgets are upheld.

Before you begin utilizing this as well, affirm that the wireless card can infuse bundles. At that point begin WEP cracking. Read the online instructional exercise on the site to know all the more about the device. In the event that you will take after steps appropriately, you will wind up getting accomplishment with this apparatus.
Get it from: http://www.aircrack-ng.org/
2- Cain & Abel :
Cain & Abel is a popular password cracking tool. This tool is developed to intercept network traffic and then discover passwords by bruteforcing the password using cryptanalysis attack methods. It can also recover wireless network keys by analyzing routing protocols. It you are trying to learn wireless security and password cracking, you should once try this tool.
Get it from: http://www.oxid.it/cain.html
3- NetStumbler :
Wpa2 Encryption Key
NetStumbler is a famous Windows tool to discover open wireless access focuses. This tool is free and is accessible for Windows. A trimmed down variant of the tool is additionally accessible. It is called MiniStumbler.
Essentially NetStumblet is utilized for wardriving, checking system designs, discovering areas with a poor system, distinguishing unapproved access focuses, and that's only the tip of the iceberg.
Be that as it may, the tool additionally has a major disadvantage. It can be effectively recognized by a large portion of the wireless interruption identification frameworks accessible. This is on account of it effectively tests a system to gather helpful data. Another weakness of the tool is that it doesn't work legitimately with the most recent 64 bit Windows OS. This is on account of the tool was last redesigned back in April 2004. It has been around 11 years since the last stable arrival of the tool.
Get it from : http://www.stumbler.net/
4- WireShark :
WireShark is the system convention analyzer. It gives you a chance to weigh what is going on in your system. You can live catch parcels and examine them. It catches parcels and gives you a chance to check information at the smaller scale level. It keeps running on Windows, Linux, OS X, Solaries, FreeBSD and others. WireShark obliges great learning of system conventions to dissect the information acquired with the tool. In the event that you don't have great learning of that, you may not discover this tool fascinating. In this way, attempt just on the off chance that you are certain about your convention information.
Get it from: https://www.wireshark.org/
5- Airjack :
Airjack is a Wi-Fi 802.11 parcel injection tool. This wireless cracking tool is extremely helpful in infusing manufactured parcels and making a system around refusal of administration assault. This tool can likewise be utilized for a man as a part of the center assault in the system.
Get it from: http://sourceforge.net/projects/airjack/
6- WepAttack :
WepAttack is an open source Linux tool for breaking 802.11 WEP keys. This tool performs a dynamic word reference assault by testing a large number of words to locate the working key. Just a working WLAN card is obliged to work with WepAttack.
Get it from: http://sourceforge.net/projects/wepattack/
Enable Wpa2 Encryption
7- CloudCracker :
CloudCracker is the online secret word cracking tool for cracking WPA ensured wi-fi systems. This tool can likewise be utilized to split distinctive secret key hashes. Simply transfer the handshake record, enter the system name and begin the tool. This tool has an immense lexicon of around 300 million words to perform.
Access it from: https://www.cloudcracker.com/
8- OmniPeek :
OmniPeek is another pleasant parcel sniffer and system analyzer tool. This tool is business and backings just Windows working frameworks. This tool is utilized to catch and dissect wireless activity. Be that as it may, it obliges you to have great information of conventions to legitimately comprehend things. Something worth being thankful for is that the tool meets expectations with the vast majority of the system interface cards accessible in business sector. This tool is utilized for system investigating. This tool additionally bolsters plugins, and 40 plugins are as of now accessible to broaden the components of the tool.
Get it from: https://www.savvius.com/products/overview/
9- Kismet:
Kismet is the wi-fi 802.11 a/b/g/n layer2 wireless system sniffer and IDS. It lives up to expectations with any wi-fi card which bolsters rfmon mode. It latently gathers bundles to recognize systems and distinguish concealed systems. It is based on customer/server measured structural engineering. It is accessible for Linux, OSX, Windows and BSD stages.
Get it from: http://www.kismetwireless.net/
10- CoWPAtty :
CoWPAtty is a computerized word reference assault tool for WPA-PSK. It keeps running on Linux OS. This system has an order line interface and keeps running on a word-list that contains the watchword to use in the assault.
Utilizing the tool is truly basic, however it is moderate. That is on account of the hash utilizes SHA1 with a seed of SSID. It implies the same secret key will have an alternate SSIM. Thus, you can't just utilize the rainbow table against all entrance focuses. In this way, the tool utilizes the secret word lexicon and produces the hack for every word contained in the word reference by utilizing the SSID.
The new form of the tool attempted to enhance the pace by utilizing a precomputed hash record. This precomputed document contains around 172000 lexicon record for around 1000 most prevalent SSIs. Yet, in the event that your SSID is not in those 1000, you are unlucky.
Get it from: http://sourceforge.net/projects/cowpatty/
In this post, I talked about 10 top wireless hacking tools. A couple of wireless hacking tools are for cracking the secret key to get unapproved access may be crime and may you get into trouble. Be that as it may, so don't use this tool for illegal purpose, simply need to get free Internet access.
The above accumulation likewise contains those tools which attempt permit you to get free Internet access. However, make sure not to utilize these tools in a unauthorised spot. As I effectively said, you ought to never utilize the WEP encryption enter in your home or wireless system. With accessible tools, it is easy breezy to split the WEP keys and access your wi-fi system.
Wireless observing and investigating tools are fundamentally for system administrators and software engineers dealing with wi-fi based programming. These tools truly help when some of your frameworks face issues in joining with the system.
Thanks for reading this article, collect from one of my google plus friend's post Sabarinath k rajenderan.



